Stuxnet Worm Analysis, Feb 2012
Great crowd turned out to hear Symantec Security Engineer Liam O’Murchu discuss the Stuxnet Virus, how it targeted Iran’s nuclear program specifically, and what effort and steps Symantec took to decode it.
Click the pictures below to see them full size.
About 35 attended this presentation in Richter Hall starting at 1900. Presentation and discussion ran until 2030.
Liam and a Symantec team of 4 to 8 engineers worked 6 months to analyze Stuxnet.
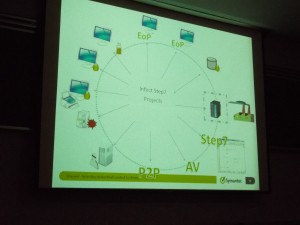
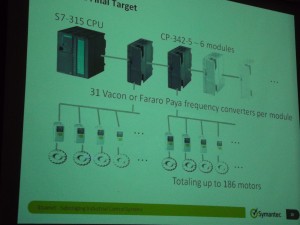
Stuxnet targeted these specific Siemens PLCs, and only when they were in a specific configuration that meant they were being used to control an array of uranium centrifuges.
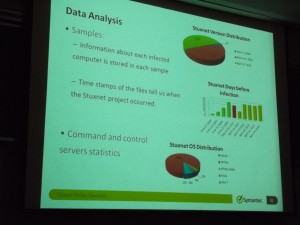
Overview of what Symantec found. The worm had three release, April 2009, March 2010, and June 2010. In frame is the presenter, Liam O’Murchu.
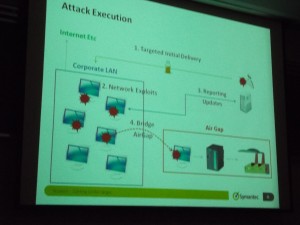
Stuxnet spread through several known exploits, such as file shares, and “phoned home” to two data collection servers, one in Denmark and one in Indonesia. A critical exploit allowed the virus to mask attacks against Siemens PLCs via the Step7 IDE/toolkit used to program the PLCs (more below). Siemen’s code also relied on hard-coded passwords to feed SCADA (telemetry) information into the master logging database.
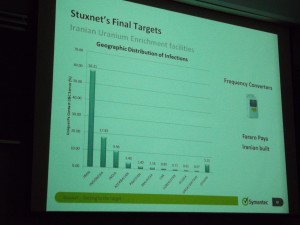
Stuxnet infected mostly Iranian machines, but was slowly spreading world-wide. It was capable of infecting all Windows 32 environments. The program is about 1.5 MB altogether.
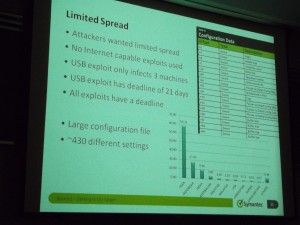
The spread of the virus was controlled by growth inhibition factors. About 430 configuration points exist in the program. For example, the program would copy itself only 3 times via USB key, then turned off that switch and erased its files on the USB keys.
The worm appended a log of where it had been to itself, so as it moved from machine to machine, it kept an audit trail. Very handy for analyzing the spread, and also useful for its designers to plot their next attack path.
The worm used three legitimate signatures (“driver signing certificates”), all stolen from tech companies in the far east. Two of them came from two firms located within blocks of each other in Taiwan.
To bridge the air gap, Stuxnet exploited a new defect in the way Microsoft Windows handled .lnk files, CVE-2010-2568 (MS10-046). Liam surmised Stuxnet got in to circulation after a spearfishing attack got the program onto a system used by a contract programmer working on PLCs for the Iranian nuclear program.
The worm’s audit trail potentially allowed it to report back from inside networks.
In addition to infecting Siemens PLC code, Stuxnet inserted a .DLL into projects built with Siemens’s Step7 PLC programmers workbench. Infected Step7 projects automatically ran the .DLL when the project archive was opened. When Step7 users used the infected workbenches to inspect the code running in the PLCs, the hacked .DLL stripped out the virus payload code, so the programmer never saw malware in the PLC’s running program.
Stuxnet targeted only PLCs running centrifuges capable of running faster than 600 kHz (which are export controlled), connected only to specific models of modules, and only in specific arrays which would indicate they were being used in a large-scale uranium centrifuge facility. The worm’s design demonstrated great care in targeting these exact configurations.
Summary.
Thanks Liam! Don Thomas, IEEE Buenaventura Section CS officer (left), presents our thanks.
Please find more detail at Symantec’s Stuxnet page.